This session is Data Security is Required. KM is Demanded. AI is Here: Armageddon or Utopia?. Peter Kaomea, CIO of Sullivan & Cromwell presents. The session description appears at the end of the post.
Session Report
Powerful forces are now coming together: KM, AI, and information security. Info sec may be the biggest driver though given cybersecurity issues.
Definitions..
KM is the process of creating, sharing, using, and managing the knowledge and info of an organization.
Info sec is process to maintain confidentiality, integrity, and availability of data.
AI is computers performing learning and decision making.
Peter does a fab job using the Police song to describe how each line in the song relates to current security considerations…
Xbox will watch your moves; bonds you break = unfriending; night you stay = Google calendar; every word = Siri or Echo; watching you = Samsung TV; move you make = smart watches; smile you make = vision systems coupled with machine learning; watching you = >5B video cameras.
—
Recent major security breaches: Panama papers and Yahoo.
Integrity + Injections: hackers inject payment order, false orders… hackers watch email re transactions and toward, inject email with payment order to wrong account (theft).
Availability: ransomeware, recent DDOS attach against Dyn.
—
Clients now wanted law firms to limit access to documents and dat. Firm used Kira to extract clauses from client security documents. They have multiple ways of saying limit access but impact is all similar. Clients increasingly also ask firms to purge data at the end of a matter or some other time specific.
—
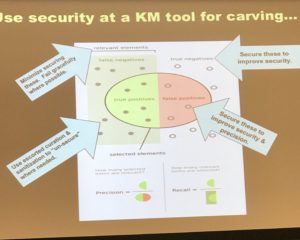
How can we reconcile info sec requirements and need to share (KM). How can we leverage security investments to help KM? Security incident and event management (SIEM) systems track everything that goes on in an organization’s systems. These look for anamolous behaviors and flags them for action (by a person).
Even in encyrpted systems, someone always has the keys. These individuals are often targeted. Even without the keys, hackers can monitor cloud system traffic and draw certain inferences, even without seeing the data.
“Enclave” is a rapidly emerging concept in security. It means pulling really sensitive data off of online systems and isolating it.
Some of the security systems contribute to KM. By watching access and considering permissions and use cases, it is possible to tailor search results..
AI and KM… you can use machines to watch user behavior, for example, ratio of sent to received email or local versus remote access. This can support both security (anamoly detection) and KM requirements.
Tapping public data re entities can help with analytics
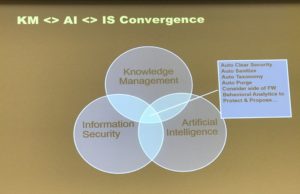
At the intersection of KM, Info Sec, and AI…
- Auto clear security… lawyer about to work on a matter, the back end can tap multiple sources and validate need for access (instead of calling aroun0
- Auto sanitize… entity extraction from documents helps sanitize for re-use. But context may still give away too much
- Auto taxonomies…
- Auto purge… use rules and/or behavior to determine when a document can be purged
- Consider which side of firewall… analyze in- and out-coming traffic and assess value relative to risk
- Behavioral analytics…. to manage risk
Session Description
Data Security is Required. KM is Demanded. AI is Here: Armageddon or Utopia?
When undeniable forces collide, the result can be massive destruction, or unimaginable power and beauty. Today, our clients require the highest quality of work product leveraging the composite capability of our respective firms – the KM promise of the last 20 years. Hacks like the Panamanian Papers illustrate the awesome responsibility entrusted in us to protect client and firm confidences. As if this weren’t enough, Artificial Intelligence and Advanced Analytics are coming of age… How can we harness these forces to have it all?
Peter Kaomea, Chief Information Officer, Sullivan & Cromwell LLP
Archives
Blog Categories
- Alternative Legal Provider (44)
- Artificial Intelligence (AI) (57)
- Bar Regulation (13)
- Best Practices (39)
- Big Data and Data Science (14)
- Blockchain (10)
- Bloomberg Biz of Law Summit – Live (6)
- Business Intelligence (21)
- Contract Management (21)
- Cool Legal Conferences (13)
- COVID-19 (11)
- Design (5)
- Do Less Law (40)
- eDiscovery and Litigation Support (165)
- Experience Management (12)
- Extranets (11)
- General (194)
- Innovation and Change Management (188)
- Interesting Technology (105)
- Knowledge Management (229)
- Law Department Management (20)
- Law Departments / Client Service (120)
- Law Factory v. Bet the Farm (30)
- Law Firm Service Delivery (128)
- Law Firm Staffing (27)
- Law Libraries (6)
- Legal market survey featured (6)
- Legal Process Improvement (27)
- Legal Project Management (26)
- Legal Secretaries – Their Future (17)
- Legal Tech Start-Ups (18)
- Litigation Finance (5)
- Low Cost Law Firm Centers (22)
- Management and Technology (179)
- Notices re this Blog (10)
- Online Legal Services (64)
- Outsourcing (141)
- Personal Productivity (40)
- Roundup (58)
- Structure of Legal Business (2)
- Supplier News (13)
- Visual Intelligence (14)